Common DKIM Setup Errors and Fixes
Email deliverability often hinges on proper DKIM (DomainKeys Identified Mail) configuration. When misconfigured, DKIM can cause emails to fail authentication, leading to spam folder placement or outright rejection. Here's what you need to know:
Key Takeaways:
- DKIM ensures email authenticity: It uses cryptographic signatures to verify that emails are from the claimed sender and remain unaltered.
- Misconfigurations are common: Errors like incorrect DNS record formats, expired keys, or body hash mismatches can disrupt email delivery.
- Cold outreach suffers without DKIM: Emails without proper DKIM setup are more likely to be flagged as spam, damaging sender reputation and reducing engagement.
Common Errors:
- Wrong DNS Record Format: Misplaced or incorrectly formatted TXT records can cause public key retrieval failures.
- Selector Issues: Duplicate or mismatched selectors lead to validation errors.
- Expired Keys: Outdated keys can invalidate email authentication.
- Body Modifications: Changes like tracking links added after signing can break DKIM signatures.
- DNS Propagation Delays: Updates to DNS records may take hours to reflect globally, causing temporary failures.
Solutions:
- Use DKIM record generators to avoid formatting mistakes.
- Assign unique selectors for each domain and verify alignment with published DNS records.
- Regularly rotate and update keys to maintain security and prevent expiration issues.
- Ensure all email modifications occur before signing to avoid body hash mismatches.
- Allow sufficient time for DNS propagation before testing new configurations.
For businesses managing multiple domains or large-scale outreach, automated tools like Infraforge simplify DKIM setup and maintenance, reducing the risk of errors and ensuring consistent email deliverability.
Most Common DKIM Setup Errors
Getting DKIM (DomainKeys Identified Mail) right is essential for keeping your emails out of spam folders and ensuring they get delivered properly. But many domains run into common setup mistakes that disrupt email authentication. Let's break down these errors and their impact.
Wrong DNS Record Format or Location
One of the most common DKIM issues? Misplacing the TXT record or using the wrong format. The correct structure should look like this: [selector]._domainkey.[yourdomain.com]. When this format is incorrect, or the record is placed in the wrong subdomain, recipient servers can’t retrieve the public key needed for authentication.
Typical mistakes include:
- Forgetting the selector entirely
- Misspelling
_domainkey - Placing the record directly on the root domain instead of a subdomain
For example, using dkim.example.com instead of default._domainkey.example.com will cause authentication to fail. Without the public key, recipient servers can’t verify your emails, which often results in them being marked as unauthenticated - and possibly ending up in spam.
Selector Problems and Duplicates
Selectors are like guides that help recipient servers find the right public key in your DNS records. But if there’s a mismatch between the selector you’ve configured and the one published, validation will fail. Duplicate selectors across multiple domains can also cause issues.
This is especially tricky for organizations managing multiple domains or email services. A common mistake is reusing the same selector name across domains or forgetting to update selectors during email system migrations. In these cases, recipient servers might pull the wrong public key or encounter conflicting records, breaking the DKIM setup.
Managing multiple selectors across third-party services or email platforms adds another layer of complexity. Without proper coordination, overlapping or conflicting configurations can disrupt DKIM authentication entirely.
Bad or Expired DKIM Keys
DKIM keys aren’t forever - they need regular upkeep. Expired keys or mismatches, like pairing a 1,024-bit public key with a 2,048-bit signing key, will lead to immediate validation failures.
Proper key management is critical to avoid these issues, which can otherwise result in emails being flagged as unauthenticated and sent to spam.
Body Hash Verification Failures
DKIM works by creating a hash of the email's content when it’s signed. If the email body gets modified after signing - say, by adding disclaimers or tracking pixels - the hash won’t match, and the signature will fail.
Here’s an example: A marketing agency found that their emails were failing DKIM validation after recipients forwarded them. The issue? Their email platform was adding tracking links after the DKIM signing process, altering the email body and breaking the cryptographic hash. The solution? Restructuring their email pipeline so all modifications happened before signing.
DNS Propagation Delays and Visibility Issues
DNS updates don’t happen instantly. When you publish or update DKIM records, it can take anywhere from minutes to hours for the changes to propagate across the internet. During this time, some recipient servers might not see the updated records, leading to inconsistent validation results.
Propagation delays vary based on your DNS provider and location. If you test immediately after making changes, you might accidentally extend these delays, creating a frustrating cycle of intermittent failures.
The best practice? Wait for full DNS propagation before sending production emails to ensure that DKIM validation works consistently.
Understanding these common errors is the first step toward fixing them, paving the way for better email authentication and deliverability.
How to Fix Common DKIM Setup Errors
Now that you're familiar with the usual pitfalls of DKIM, let's dive into practical, step-by-step solutions to get your email authentication back on track.
Fixing DNS Record Format and Location
First things first - your DNS record needs to follow this exact format: [selector]._domainkey.[yourdomain.com]. Even a tiny error in this structure can lead to failed authentication.
To sidestep potential mistakes, use a DKIM record generator instead of trying to create the record manually. Once generated, copy and paste the values directly into your DNS management console to avoid transcription errors.
Double-check that you're placing the record in the correct subdomain. It should always go under the specific selector subdomain - not the root domain or any other location. After publishing the record, test it with a DKIM checker to confirm it's visible and properly formatted. For example, a university successfully resolved email validation issues by fixing a selector mismatch.
Finally, manage your selectors carefully to prevent conflicts.
Managing Selectors for Multiple Domains
When juggling multiple domains, selector conflicts can become a headache. To avoid this, assign unique selectors to each DKIM record.
Make sure the selector in your email server settings matches the one published in DNS exactly. Establishing a naming convention - like "gs2024-domain1" or "mail-companyname" - can help keep your selectors organized and unique.
Before making big changes, such as migrating email systems or adding a new domain, audit your current selectors. This simple step can prevent duplicate selectors from disrupting your email service.
Once your selectors are sorted, you can focus on keeping your keys up-to-date.
Updating and Rotating DKIM Keys
Regularly rotating your DKIM keys is crucial for maintaining secure email authentication. Aim to rotate keys annually or whenever security demands it.
Here’s a quick breakdown of the rotation process: generate a new key pair, publish the new public key in DNS under a new selector, update your mail server to use the new private key, and, once DNS propagation is complete, remove the old key.
Pay close attention to the bit length of your keys. A common issue arises when a 1,024-bit public key is published, but a 2,048-bit private key is used for signing. This mismatch will cause validation errors. Always ensure your key lengths align during upgrades.
To stay ahead of potential problems, set up reminders or use scheduling tools to track key expiration dates. Expired keys can lead to all outgoing emails failing validation, so proactive monitoring is essential.
Maintaining Message Integrity After Signing
Body hash verification errors happen when email content is altered after DKIM signing. To prevent this, make sure no changes are made to the email once it’s signed.
Include all headers - like tracking pixels, disclaimers, and footers - before the signing process. Avoid using services that modify emails after they’ve been sent. If modifications are unavoidable, configure them to occur before signing.
For forwarded emails, let recipients know that appended content might invalidate the signature. Using services designed to preserve DKIM signatures during forwarding can help maintain message integrity.
Additionally, use relaxed canonicalization and sign all required headers to reduce the risk of body hash verification failures.
Solving DNS Propagation and Visibility Problems
DNS propagation delays can’t always be avoided. Be patient and wait for full propagation before activating a new DKIM key.
Global DNS lookup tools can help you check which servers have updated and which are still catching up. If propagation seems unusually slow, review your DNS provider's Time To Live (TTL) settings. A TTL of around 3,600 seconds (1 hour) often strikes a good balance between speed and efficiency.
To monitor DKIM performance, keep an eye on DMARC reports. While testing specific DNS servers can provide quick insights, always wait for global propagation before relying on the setup for production emails.
For a smoother experience, platforms like Infraforge can simplify these steps by automating the technical setup for DMARC, SPF, and DKIM configuration. They follow industry standards to reduce the risk of errors.
Infraforge: Automated DKIM Setup and Management
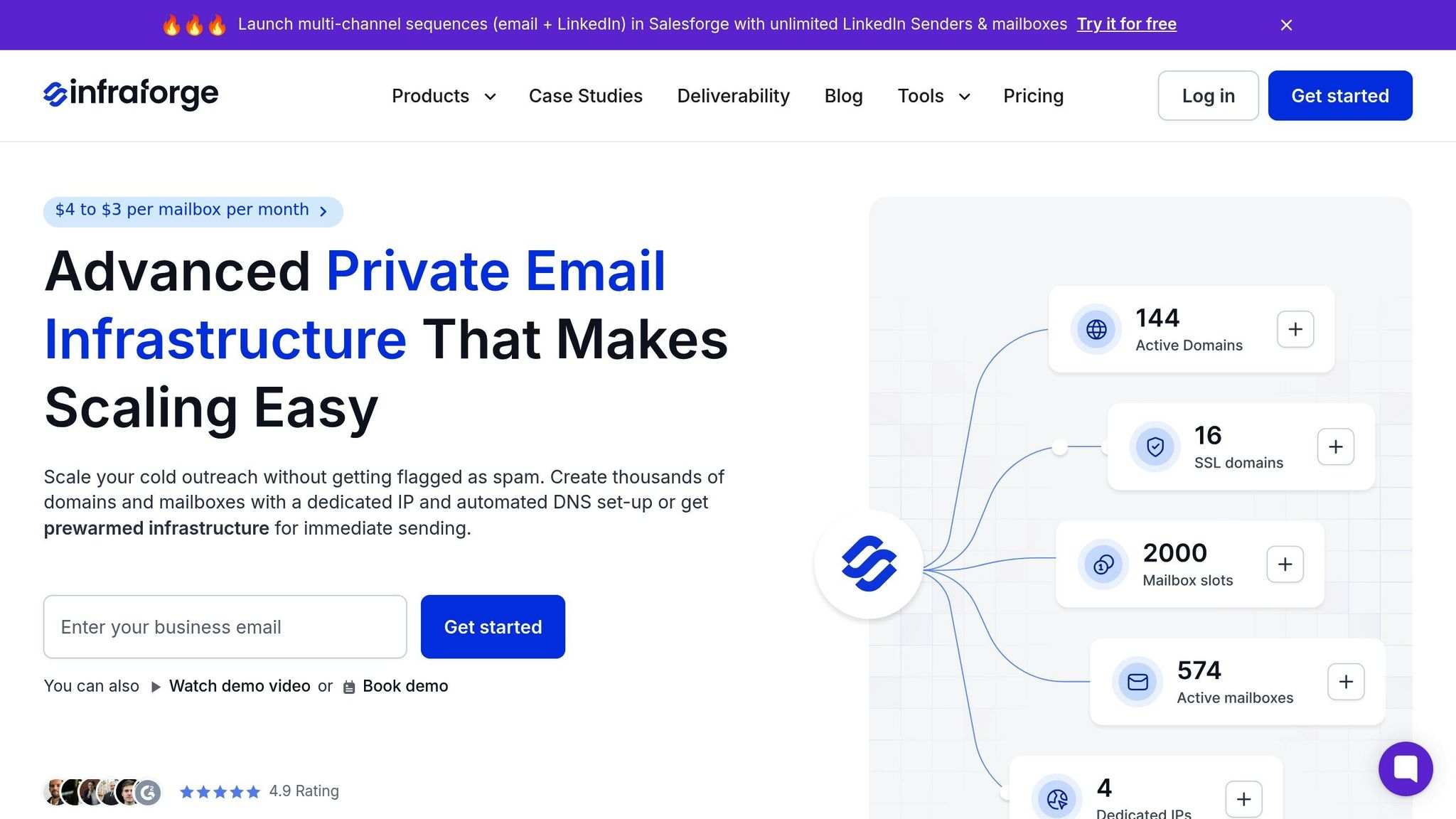
After exploring common DKIM errors and their manual fixes, Infraforge emerges as a streamlined, automated solution that eliminates these challenges altogether.
Setting up DKIM manually can be tedious and prone to mistakes. Infraforge simplifies the entire process, automating configuration and management - key for ensuring reliable cold email outreach.
Automated DNS Setup and Error Prevention
Infraforge takes the guesswork out of setting up DKIM records. When you add a new domain, it automatically generates and publishes properly formatted DKIM records based on industry standards. This automation ensures that common issues like formatting errors, selector conflicts, or misplaced records are avoided. By adhering to the precise [selector]._domainkey.[yourdomain.com] structure, Infraforge reduces the risk of transcription mistakes that could compromise authentication.
With Infraforge, you can activate a domain and mailbox in just 5 minutes - far quicker than traditional methods. Pre-configured templates handle DKIM, SPF, and DMARC records, making authentication seamless. Plus, the system includes real-time deliverability monitoring and proactive alerts to address potential issues before they disrupt your campaign.
Key Rotation and Real-Time Monitoring
Infraforge automates DKIM key rotation, scheduling updates and revising DNS records without manual intervention. Its real-time monitoring keeps tabs on authentication results, DNS propagation, and key rotation history, while issuing instant alerts for any delays in visibility. Regular key updates are essential for maintaining email security, reducing the risk of key compromise, and meeting industry guidelines. Infraforge ensures that expired or outdated keys won’t lead to DKIM failures or open the door to spoofing attacks.
If new DKIM records aren't immediately visible to external resolvers, Infraforge sends alerts, helping you maintain consistent authentication and optimal deliverability - even during setup or key rotation.
Integration with The Forge Stack Tools
Infraforge seamlessly integrates with Salesforge and Warmforge, creating a unified system for managing DKIM, SPF, and DMARC records while optimizing outreach and deliverability testing.
This integration allows authentication data to flow automatically between tools. For example, when Warmforge sets up your domains and mailboxes, it leverages the DKIM configurations already established by Infraforge’s automation. This ensures your domains are properly warmed up and ready for outreach, aligning with best practices for DKIM management.
"During my time at a Fortune 500 company and now across all our products, Infraforge has been my go-to solution for Email Infrastructure. Its deliverability and impact are unmatched. If you're serious about outreach and want the best tool in the market, Infraforge is the only choice."
– Rahul Lakhaney, Former VP, Gartner, now CEO @ Enrich.so and Maximise
Best Practices for DKIM Management
Keeping DKIM management up to date is crucial for preventing failures and maintaining strong email deliverability. By monitoring key metrics like DKIM pass/fail rates, deliverability scores, and authentication results, organizations can spot and address issues before they disrupt campaigns. These practices build on earlier strategies to ensure consistent DKIM performance over time.
Regular DNS Record Checks
Outdated or misconfigured DNS records are a common cause of DKIM failures. Regularly auditing your DNS setup can catch problems like formatting errors, selector mismatches, or propagation delays before they interfere with email delivery. According to a 2023 Valimail survey, over 30% of organizations faced at least one DKIM-related deliverability issue in the past year. Additionally, industry data shows that up to 20% of DKIM failures result from DNS misconfiguration or propagation delays.
For organizations managing multiple domains, it’s vital to maintain unique and well-documented selectors. This prevents conflicts and ensures that each sender is properly authenticated.
Scheduled Key Rotation and Expiry Monitoring
Rotating DKIM keys every 6–12 months is a key security measure and aligns with established best practices. Expired or compromised keys can lead to authentication failures and increase the risk of spoofing. Delays in updating keys or sending emails prematurely during DNS propagation often result in temporary authentication issues.
Automating key rotation can help reduce human error. Setting up alerts for upcoming key expirations ensures you’re prepared to update them on time. To avoid temporary failures, always wait for complete DNS propagation before sending emails with newly signed keys.
Ongoing Deliverability Testing
Effective DKIM management goes beyond key rotation - it also requires continuous testing to safeguard email authentication. Monitoring DMARC reports provides valuable insights into DKIM performance and helps identify unauthorized sending sources. These reports can alert you to authentication failures and highlight trends in deliverability.
Platforms like Warmforge offer dashboards and analytics that visualize authentication metrics, enabling data-driven decisions for managing DKIM. These tools monitor results in real time and can quickly detect DKIM-related issues, ensuring they don’t disrupt your campaigns.
Regular testing also uncovers issues with message integrity. For example, email forwarding or modifications by intermediate servers can break DKIM signatures, even if the original setup is correct. Tracking spam complaint rates alongside authentication metrics provides a more complete view of email performance, as increases in DKIM failures often correlate with reduced deliverability.
Conclusion: Reliable DKIM Setup for Email Outreach
Getting DKIM configuration right is essential for effective cold email outreach. As much as 20% of business emails fail DKIM validation due to expired or misconfigured keys, which can send your carefully crafted messages straight to spam instead of inboxes. Properly authenticated emails, on the other hand, ensure your outreach efforts land where they’re supposed to - your recipient's inbox.
Tips to Avoid DKIM Errors
Ensuring reliable DKIM authentication starts with addressing common setup issues before they arise. Here are some best practices:
- Use record generators to eliminate formatting mistakes.
- Follow a clear naming convention for selectors to avoid conflicts, especially when managing multiple domains.
- Allow sufficient time for DNS propagation before deploying new keys - this is a step that's often rushed in the eagerness to launch campaigns.
- Rotate your DKIM keys every 6–12 months to keep your authentication secure.
- Avoid modifying emails after they’re signed, as this can break the DKIM signature.
- Ensure all email headers are signed and that DNS records are published under the correct selector to prevent validation failures.
When combined with automation tools, these practices can simplify DKIM management and reduce the risk of errors.
How Infraforge Simplifies DKIM Management
Infraforge takes the hassle out of DKIM management by automating the entire process. From configuring DKIM, DMARC, and SPF records to ensuring alignment with industry standards, Infraforge handles it all. This is especially valuable for businesses juggling multiple domains. With a quick, 5-minute setup for domains and mailboxes, Infraforge allows you to focus on your outreach strategy instead of wrestling with DNS configurations.
Rahul Lakhaney, Former VP at Gartner and now CEO of Enrich.so, underscores the platform's value:
"Its deliverability and impact are unmatched. If you're serious about outreach and want the best tool in the market, Infraforge is the only choice."
Infraforge goes beyond just setup. Through its integration with The Forge Stack, it offers continuous authentication monitoring with tools like Warmforge, providing real-time analytics on deliverability. This proactive approach helps identify and resolve DKIM issues before they disrupt your campaigns, ensuring your outreach efforts remain effective over the long haul.
FAQs
How can I prevent my DKIM keys from expiring and causing email authentication issues?
To prevent issues stemming from expiring DKIM keys, it's crucial to keep an eye on their expiration dates and renew them ahead of time. Automating your DNS record management can make this process much easier and help ensure your settings remain current. Tools like Infraforge offer a secure, automated way to handle these tasks, making it simpler to maintain reliable email authentication.
How can I confirm that my DKIM DNS records are set up correctly?
To make sure your DKIM DNS records are set up correctly, begin by comparing the record values with the details provided by your email service or domain provider. Look out for typos, missing characters, or formatting errors in the public key.
If you're using Infraforge, the platform takes the hassle out of this process. It automates the setup of DKIM, SPF, and DMARC records, ensuring they meet industry standards. This not only reduces the risk of manual mistakes but also helps keep your email deliverability on track.
How does Infraforge simplify managing DKIM, SPF, and DMARC records?
Infraforge simplifies the management of DKIM, SPF, and DMARC records by automating their setup and ensuring they align with industry standards. It also supports bulk DNS updates, making adjustments fast and minimizing the risk of errors.
By integrating smoothly with your current tools, Infraforge takes the hassle out of email authentication. This not only saves time but also boosts email deliverability and helps maintain a solid sender reputation.