How DNS Monitoring Protects Email Deliverability
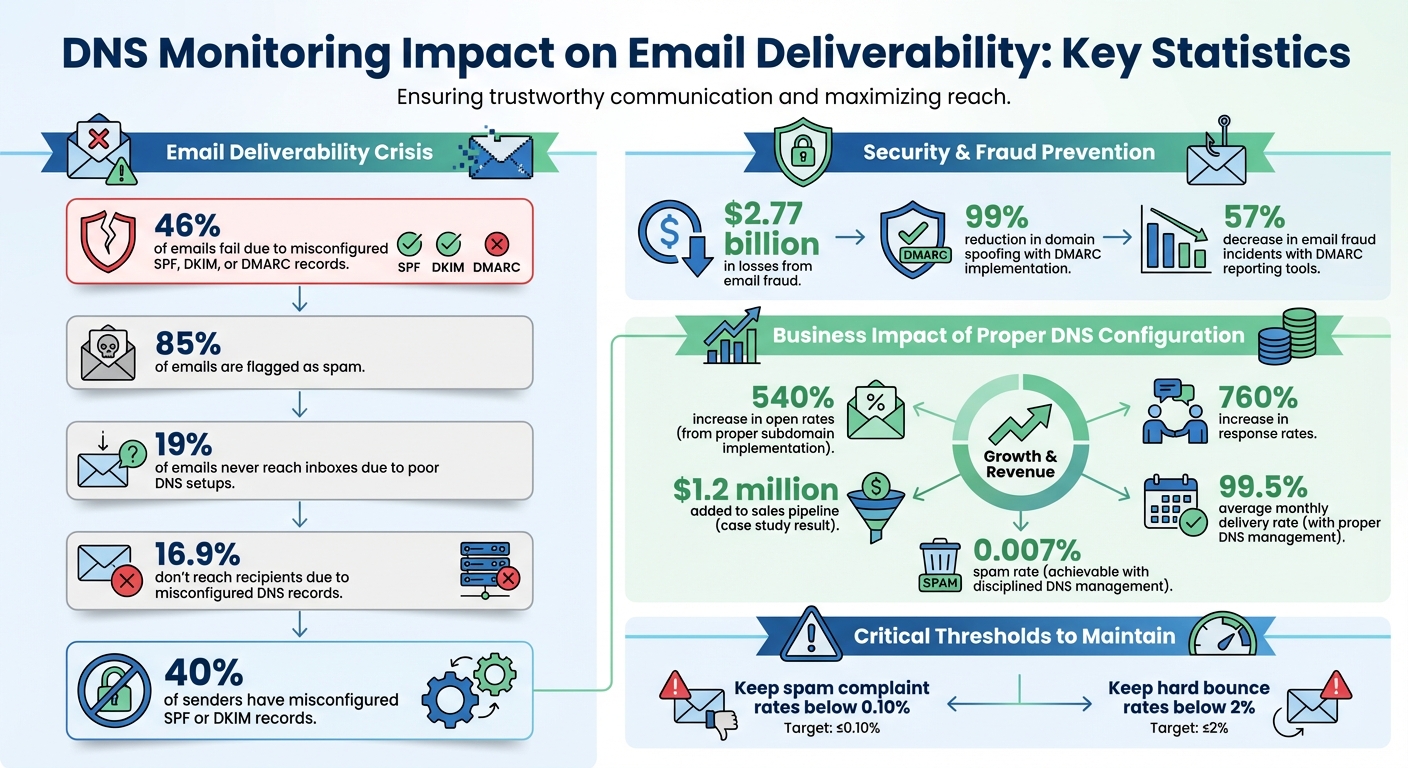
DNS monitoring is critical for ensuring your emails reach inboxes instead of getting flagged as spam. Misconfigured SPF, DKIM, or DMARC records can lead to 46% of emails failing to deliver, harming sender reputation and revenue. With email fraud causing over $2.77 billion in losses, proper DNS setup is no longer optional - it’s essential for email security and success.
Here’s why DNS monitoring matters:
- Email deliverability: Misconfigured DNS records result in 16.9% of emails not reaching recipients.
- Security: DMARC implementation reduces domain spoofing by 99% and email fraud incidents by 57%.
- Business impact: Improved DNS configurations can boost open rates by up to 540% and add millions to sales pipelines.
To maintain deliverability, focus on key DNS records like SPF, DKIM, and DMARC. Regular monitoring, tools like Infraforge, and routine audits help catch errors, protect your domain, and improve email performance. Start with a DMARC policy (p=none) to collect data, then gradually enforce stricter rules for better results.
DNS Monitoring Impact on Email Deliverability: Key Statistics
Why DNS Monitoring Matters for Email Deliverability
DNS monitoring acts as the bridge between your domain and your recipients' inboxes. Without it, even the most carefully crafted emails can end up in spam folders. The numbers tell the story: 85% of emails are flagged as spam, often due to misconfigured DNS settings. Additionally, 19% of emails never reach inboxes because of poor DNS setups. These issues arise when DNS records fail, as explained below.
How Authentication Failures Affect Deliverability
Errors or misconfigurations in DNS records can cause email providers to treat your domain as a potential threat. Something as simple as a typo in an SPF record can open the door for spammers to hijack your domain’s reputation, sending harmful emails under your name. If your SPF record exceeds the 10-lookup limit, it results in a permerror, which invalidates the authentication process.
Once these errors associate your domain with spam, providers like Gmail and Outlook tighten their filters, often leading to blocklisting. Recovering from this kind of damage can be a lengthy and frustrating process - a situation many marketers dread. Alarmingly, 40% of senders have misconfigured SPF or DKIM records, making these errors one of the top contributors to spam-related issues.
Business Benefits of DNS Monitoring
Staying on top of DNS configurations doesn’t just prevent email disasters - it can actually boost your business outcomes. Regular DNS monitoring allows you to identify and fix problems before they impact your sender reputation. For example, a B2B software company that implemented subdomains tailored to specific industries saw impressive results: open rates climbed to 32% (a 540% increase), and response rates rose to 4.3% (a 760% increase). These improvements directly contributed to $1.2 million in new sales pipeline growth.
"Deliverability is a measure of the health of your email marketing program, so it's important to do regular check-ups on your domain, IP, and authentication."
- Carin Slater, Manager of Lifecycle Email Marketing, Litmus
Better deliverability leads to higher inbox placement rates, which in turn drive more opens, clicks, and revenue. To protect your sender reputation, aim to keep spam complaint rates below 0.10% and hard bounce rates below 2%. DNS monitoring helps you achieve these goals by catching configuration issues before they spiral into bigger problems. In short, consistent monitoring is key to maintaining both the security and success of your email campaigns.
Key DNS Records for Email Authentication
Email authentication depends on a few critical DNS records working together seamlessly. When these records are properly set up and monitored, they confirm the legitimacy of your emails, signaling to receiving servers that your messages are trustworthy. On the flip side, misconfigured or missing records can result in emails being flagged as spam or even rejected outright. Let’s break down the essentials of configuring and monitoring these DNS records to ensure strong email authentication.
SPF, DKIM, and DMARC Records
At the heart of email authentication lies the "Three-Layer System": SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance).
- SPF acts like a guest list for your domain, specifying which mail servers are allowed to send messages on your behalf.
- DKIM uses cryptographic signatures to ensure that the message hasn’t been altered in transit, functioning like a tamper-proof seal.
- DMARC enforces policies for handling emails that fail SPF or DKIM checks, providing an additional layer of protection.
Major ISPs now consider email authentication a must-have for ensuring your emails land in inboxes. With cybercriminals increasingly using AI to mimic legitimate brands, SPF, DKIM, and DMARC have become essential tools for filtering out fraudulent emails. In fact, organizations using DMARC reporting tools report a 57% drop in email fraud incidents, while DMARC implementation can reduce domain spoofing by 99%.
| Protocol | Primary Function | What It Protects | Key Limitation |
|---|---|---|---|
| SPF | Authorizes sending IPs | Blocks unauthorized servers from sending as your domain | Limited to 10 DNS lookups; complex setups may need record flattening |
| DKIM | Adds cryptographic signatures | Verifies message integrity and authenticity | Requires periodic key rotation (every 6–12 months); use 2048-bit RSA keys |
| DMARC | Enforces authentication policies | Guides receivers on handling failed SPF/DKIM checks | Depends on properly configured SPF and DKIM |
To maximize security, configure DKIM with 2048-bit RSA keys to guard against modern cryptographic threats. Regularly rotate your keys every 6–12 months to maintain security and demonstrate good practices to mailbox providers. For SPF records, stay within the 10 DNS lookup limit by using record flattening techniques or dynamic SPF tools, especially if multiple services send emails on your behalf.
MX Records and Reverse DNS (PTR)
MX (Mail Exchange) records are critical for routing incoming emails to the correct servers for your domain. If MX records are misconfigured, incoming emails may fail to reach their destination.
Reverse DNS (rDNS) relies on PTR records to map your sending IP address back to a domain name. This process, known as Forward-Confirmed Reverse DNS (FCrDNS), ensures that your PTR record resolves to a domain, and that the domain’s A record resolves back to the same IP. This verification helps receiving servers confirm that your emails are coming from a legitimate source, not a spammer using a random IP.
| DNS Record Type | Purpose | Example Configuration |
|---|---|---|
| MX Record | Routes inbound email | priority 10 → mail.yourdomain.com |
| PTR Record | Maps IP to domain (rDNS) | 123.45.67.89 → mail.yourdomain.com |
| A Record | Maps domain to IP | mail.yourdomain.com → 123.45.67.89 |
Each sending subdomain (e.g., outreach.example.com) needs its own MX record and rDNS setup. Avoid using dynamic IP addresses for mail servers, as they frequently change and may lack stable PTR records, leading to delivery issues. Watch for SMTP errors like 421 and 554, which often indicate rDNS misconfigurations. Keep in mind that updates to MX and PTR records can take up to 48 hours to propagate globally, during which email delivery might be inconsistent.
How to Set Up DNS Monitoring
To get started with DNS monitoring, the first step is identifying all the email-sending services you use, such as CRMs, marketing platforms, and helpdesk tools. Once identified, verify the core authentication records - SPF, DKIM, and DMARC - and monitor your DNS settings regularly. This early detection of unauthorized changes is essential for maintaining email deliverability and protecting your sender reputation.
For DKIM, you’ll need to generate a key pair, publish the public key in your DNS, and configure your mail server to sign outgoing messages. While manual configuration can be tedious and prone to errors, automated platforms like Infraforge simplify the process. With features like one-click bulk updates and built-in validation, Infraforge can cut setup time to less than five minutes and help you avoid costly mistakes.
Tools for DNS Monitoring and Alerts
Specialized tools make DNS monitoring more manageable by providing clear insights and real-time notifications. For DMARC monitoring, tools like Postmark offer weekly summaries, while Dmarcian and ZeroBounce provide real-time alerts for issues like authentication failures or spoofing attempts. Valimail, on its free tier, offers unlimited email monitoring, with enforcement features available on paid plans.
If you need broader DNS infrastructure monitoring beyond email, enterprise-grade tools like Datadog, SolarWinds, and Catchpoint are excellent options. These tools monitor overall DNS health and can alert you instantly if records are modified or deleted.
Once you have the right tools in place, the next step is moving from monitoring to active enforcement to secure your email infrastructure.
Moving from Monitoring to Enforcement
Begin with a DMARC policy set to p=none to collect data without affecting email delivery. After two to four weeks of analyzing reports, gradually transition to p=quarantine. Once you’re confident in the setup, move to p=reject to block unauthorized emails entirely.
For example, a SaaS company reduced spam complaints by 41% within 90 days after transitioning from p=none to p=reject based on DMARC data analysis. This phased approach minimizes disruptions to legitimate email traffic while significantly improving protection against spoofing. Additionally, if you plan to implement BIMI (which displays your brand logo in recipients’ inboxes), you’ll need a DMARC policy of at least p=quarantine.
Common DNS Issues and How to Fix Them
DNS misconfigurations can wreak havoc on email deliverability, even with monitoring in place. Problems like syntax errors, missing records, or outdated configurations often arise after infrastructure changes, leading to authentication failures and emails landing in spam folders. Let’s dive into some common DNS issues and how to address them effectively.
Inconsistent Subdomain Configurations
When subdomains are used for sending emails but lack proper SPF, DKIM, and DMARC records, authentication can fail. This often happens when subdomains don’t have their own dedicated MX records, which are essential for email delivery.
To fix this, start by auditing each email-sending subdomain to ensure they have complete authentication records. For instance, if your root domain has an SPF record like v=spf1 include:_spf.google.com ~all, your subdomain should have a similar or appropriately customized configuration. The same rule applies to DKIM selectors and DMARC policies. Tools like Infraforge can simplify this process by automating subdomain configurations across multiple domains, minimizing manual errors. Additionally, check for outdated or missing records that could affect email authentication.
Outdated or Missing DNS Records
Switching email providers or services often requires updating DNS records. If SPF records are outdated or PTR records are missing, emails may fail authentication. Syntax errors - like having multiple SPF records, missing spaces between mechanisms, or exceeding the 10-lookup limit - can also cause spf=permerror errors, leading to emails being flagged or rejected.
Here’s a quick breakdown of common issues:
| Record Type | Common Syntax Errors | Impact |
|---|---|---|
| SPF | Multiple records, missing v=spf1, no spaces, exceeding 10-lookup limit |
spf=permerror; emails flagged as spam or rejected |
| DKIM | Multiple selectors for one key, truncated keys, missing semicolons, weak 1,024-bit keys | Signature verification fails; authentication collapses |
To resolve these issues, always audit your DNS records when changing providers or adding services. Use validation tools to ensure records are correct. For PTR records, confirm they match your sending IPs. Consolidate SPF records to avoid multiple entries. For DKIM, publish public keys correctly in your DNS and use 2,048-bit keys for stronger security.
DNS Configuration Drift After Infrastructure Changes
Changes in infrastructure - like migrating providers, scaling systems, or adding sending IPs - can lead to configuration drift. This happens when DNS records no longer align with your actual setup. For example, teams might update infrastructure but forget to adjust DNS records, or automated systems might overwrite manual changes. The result? Failed email authentication and lower deliverability rates.
To avoid this, verify your DNS records immediately after any infrastructure change. Confirm that your SPF record includes all new IPs, DKIM keys are properly published, and DMARC policies remain intact. For organizations managing multiple domains or scaling rapidly, manual tracking can be overwhelming. Automated DNS management platforms, such as Infraforge, can help by syncing DNS records with infrastructure changes in real time, ensuring everything stays up-to-date without manual intervention.
Maintaining DNS Health for Long-Term Deliverability
Keeping your DNS in top shape isn’t a one-and-done task. Over time, even secure configurations can drift, putting your email authentication and deliverability at risk.
Routine DNS Audits
Regular audits are key to ensuring long-term email deliverability. Aim to perform quarterly audits of all email-related DNS records. During these audits, check for syntax errors, outdated references to providers, and records that no longer match your current infrastructure. For non-email subdomains, use restrictive SPF records (v=spf1 -all) to block spoofing attempts. It's also crucial to ensure your SPF records stay within the 10-DNS-lookup limit to avoid issues. If you’re managing multiple domains, automated tools like Infraforge can make life easier by continuously validating configurations and flagging potential problems early.
DMARC Report Analysis
DMARC reports are a goldmine of insights into who’s sending emails on your behalf - both legitimately and otherwise. Review these reports monthly to spot authentication failures, spoofing attempts, or discrepancies in sending sources. When you find failures, dig into the root causes, such as missing or misconfigured records, or unauthorized senders. Use this information to gradually move your DMARC policy from p=none (monitor mode) to stricter enforcement levels like p=quarantine or p=reject once all legitimate issues are resolved. This proactive approach strengthens your DNS management and bolsters email security.
Using Reliable DNS Hosting Providers
Once you’ve established solid auditing and monitoring routines, choosing the right DNS hosting provider becomes critical. Your hosting provider directly affects email deliverability. Default DNS management from domain registrars often falls short, lacking the performance, redundancy, and advanced features needed for robust authentication. Instead, consider specialized providers like Cloudflare, Google Public DNS, or Amazon Route 53. These platforms offer better uptime and performance. Before committing, ensure the provider supports critical features like underscores in hostnames (for _domainkey and _dmarc records) and complies with standards like RFC 6376 (DKIM) and RFC 7489 (DMARC). Look for advanced capabilities such as CNAME flattening, which simplifies complex setups by allowing CNAME records at the root domain without interfering with MX records.
As Jennifer Nespola Lantz, VP of Industry Relations & Deliverability at Kickbox, explains: "The DNS (domain name server) is the foundation of the internet, which means it's the foundation of email".
"DNS is fragile. It's a 'set it and forget it' system - until something goes wrong. And when it does, the consequences are immediate and painful." - Matthew Vernhout, Principal Email Advisor, Email Industries
Conclusion
DNS monitoring plays a key role in ensuring your emails make it to the inbox instead of being flagged as spam. Without properly configured and consistently monitored SPF, DKIM, and DMARC records, your emails are at risk of being sidelined by major providers like Gmail, Yahoo, and Microsoft, ultimately harming your sender reputation.
When done right, disciplined DNS management delivers tangible results. For instance, one company reported an average monthly delivery rate of 99.5% while keeping spam rates as low as 0.007%. Achieving similar outcomes is possible when DNS management is treated as a continuous effort rather than a one-time task.
To get started, begin by auditing your DNS records with tools like MXToolbox, DMARC Analyzer, or Google Admin Toolbox. Create a regular monitoring routine that includes checking authentication statuses, tracking delivery metrics, and analyzing DMARC reports. This helps you identify unauthorized activity or configuration issues before they disrupt your email campaigns.
For businesses managing multiple domains or scaling email operations, automating DNS management is often the smarter choice. Services like Infraforge can handle SPF, DKIM, DMARC, and reverse DNS setup in just minutes, replacing hours of manual work. With features like dedicated IPs, pre-warmed domains, and built-in monitoring, Infraforge helps businesses achieve inbox placement rates as high as 98–99%. Plus, it reduces operational risks - critical when IT downtime can cost companies around $5,600 per minute.
FAQs
How does DNS monitoring help improve email deliverability?
DNS monitoring is essential for making sure your emails end up in the inbox instead of being flagged as spam. It keeps a close eye on critical records like SPF, DKIM, DMARC, and reverse DNS (rDNS) to ensure they’re set up correctly. If there’s a misconfiguration or an issue that could damage your sender reputation, DNS monitoring catches it right away.
By spotting and fixing these problems early, DNS monitoring helps protect your domain’s reputation, avoids spam filter blocks, and boosts your email deliverability rates. Consistent monitoring keeps your email setup running smoothly, ensuring reliable and effective communication.
What happens if my SPF, DKIM, and DMARC records aren’t set up correctly?
If your SPF, DKIM, and DMARC records aren’t set up correctly, your emails are at a much higher risk of being flagged as spam - or even blocked altogether. This can seriously hurt your email deliverability, making it harder to connect with the people you’re trying to reach.
On top of that, skipping these records leaves your domain open to spoofing and phishing attacks. This not only damages your sender reputation but also puts your domain at risk of being used in scams. Configuring these records correctly is a crucial step to protect your domain, maintain trust, and ensure your emails make it to inboxes rather than spam folders.
How does DNS monitoring protect your domain and improve email deliverability?
DNS monitoring acts as a protective shield for your email-sending domain, keeping a close eye on vital authentication records like SPF, DKIM, and DMARC. These records play a crucial role in making sure that only authorized servers can send emails on your behalf, which helps prevent domain spoofing and phishing attacks that could damage your reputation.
By spotting and notifying you of any unusual changes, DNS monitoring stops fraudulent activity before it can harm your domain. It also offers helpful insights into how well your email authentication is performing, ensuring you maintain a solid sender reputation and avoid the dreaded spam folder. Tools like Infraforge simplify this process with features like dedicated IPs, automatic DNS setup, and real-time monitoring, giving you peace of mind while keeping your email campaigns secure and effective.