SPF, DKIM, DMARC: Compliance Monitoring Basics
Email authentication is no longer optional - it's mandatory if you're sending over 5,000 emails daily, as required by Gmail and Yahoo since February 2024. Without proper configuration of SPF, DKIM, and DMARC, your emails may land in spam folders or be blocked entirely. These protocols protect against domain spoofing, a tactic responsible for over 90% of email attacks, contributing to $55 billion in global losses from Business Email Compromise (BEC) scams.
Here’s what you need to know:
- SPF defines which IPs can send emails on your behalf.
- DKIM ensures email integrity using cryptographic signatures.
- DMARC enforces alignment between SPF/DKIM and the visible "From" address, while providing reports to monitor email traffic.
Setting up these protocols is just the start. Monitoring and maintaining them is essential to avoid misconfigurations that can harm email deliverability. Tools like Infraforge simplify this process by automating DNS setup and providing real-time monitoring, cutting down setup time and reducing errors.
Actionable Steps:
- Configure SPF, DKIM, and DMARC for your domains.
- Start with a DMARC
p=nonepolicy to monitor email traffic. - Gradually enforce stricter policies (
p=quarantine,p=reject) as you resolve issues. - Use tools to automate DNS management and monitor compliance.
Proper email authentication boosts deliverability, protects your domain from spoofing, and ensures your messages reach the inbox.
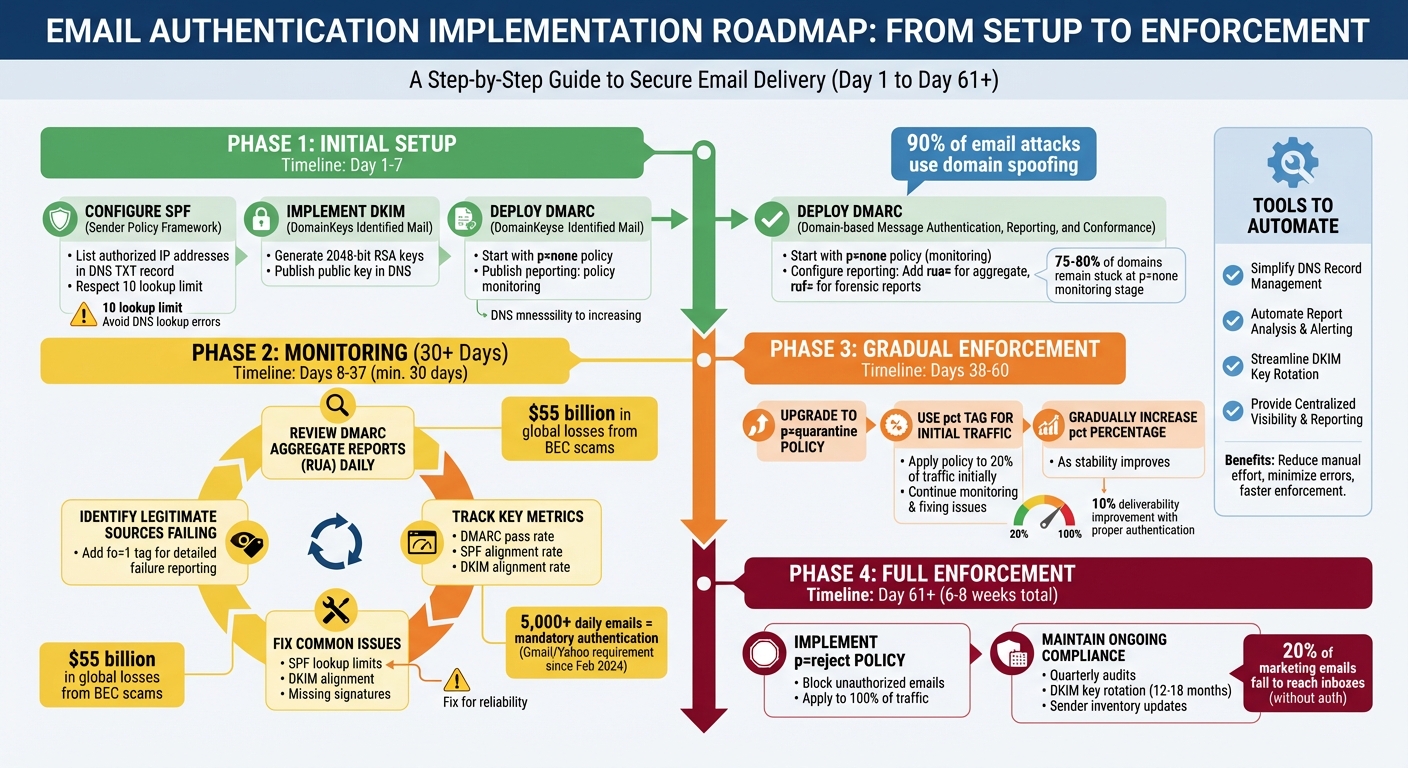
Email Authentication Setup and Enforcement Roadmap: SPF, DKIM, and DMARC Implementation Steps
SPF, DKIM, and DMARC Basics
Email authentication works like a three-layer security system: SPF, DKIM, and DMARC. Each plays a unique role. SPF specifies which IPs are allowed to send emails on your behalf. DKIM ensures the email hasn’t been tampered with during transit. DMARC ties it all together by verifying that the "From" address matches the authenticated domain.
When used alone, these protocols have gaps. SPF only checks the envelope sender (the MAIL FROM address) and doesn’t secure the "From" address visible to recipients. DKIM verifies the message's integrity and its sending domain but doesn’t enforce alignment with the visible sender. DMARC steps in to require that the domain in the "From" header aligns with the domain validated by SPF or DKIM. With these basics in mind, let’s dive deeper into each protocol.
SPF: Sender Policy Framework
SPF works through a DNS TXT record that lists which IPs are authorized to send emails for your domain. However, it has its limitations. For instance, SPF has a 10-DNS lookup limit, which can cause issues when multiple services or forwarding servers are involved. This often leads to authentication failures, especially in complex setups. For this reason, SPF is most effective when paired with DKIM.
DKIM: DomainKeys Identified Mail
DKIM adds a digital signature to your email headers using public-key cryptography. Here’s how it works: the sending server signs the email with a private key, and receiving servers verify it using a public key stored in your DNS records. This process confirms two things: the email is from an authorized source, and its content hasn’t been altered during delivery.
DKIM also allows for flexibility. You can use multiple selectors to manage different keys for subdomains. Plus, it employs a process called canonicalization (either relaxed or simple) to tolerate minor changes, like formatting adjustments or whitespace edits, ensuring legitimate emails still pass verification.
DMARC: Domain-based Message Authentication, Reporting, and Conformance
DMARC builds on SPF and DKIM by enforcing alignment - a rule that the domain in the visible "From" address must match the domain authenticated by SPF (via the Return-Path) or DKIM (via the d= tag). You can set this alignment to "strict" (requiring an exact match) or "relaxed" (allowing subdomains).
DMARC also provides valuable feedback. It generates two types of reports: aggregate reports (RUA) for high-level insights and forensic reports (RUF) for detailed issue tracking. These reports help identify misconfigurations and detect spoofing attempts.
"The end goal is ideally a policy of p=reject. That's what DMARC is for. Ensuring that your domain cannot be spoofed and protecting our mutual customers from abuse."
- Marcel Becker, Senior Director of Product, Yahoo
Despite DMARC’s benefits, many domains - between 75% and 80% - struggle to move beyond the monitoring stage (p=none) to enforcement modes like quarantine or reject. This often happens because legitimate email sources fail authentication, and resolving the issues with SPF or DKIM can be challenging. Understanding these protocols is essential for proper configuration and monitoring, as we’ll explore further in the next section.
How to Configure Email Authentication for Monitoring
Setting up email authentication is key to effective monitoring. By correctly configuring SPF, DKIM, and DMARC, you can gather actionable data and avoid common issues that could cause legitimate emails to fail delivery.
Setting Up SPF Records
An SPF record is a TXT entry in your DNS (don’t use the outdated "SPF" record type) that specifies which IP addresses are allowed to send emails on behalf of your domain. Keep in mind that SPF has a 10 DNS lookup limit. Start by listing all your email-sending sources - this includes your mail server, marketing platforms, CRM tools, and any third-party services. If multiple services are from the same provider, check if they offer a single include: statement to simplify your setup. For more complex configurations, consider using IP ranges instead of listing individual addresses.
Choose the right qualifier for your SPF record. Start with ~all (soft fail) during the initial phase. This marks unauthorized emails as suspicious but doesn’t reject them outright, giving you time to identify and fix any issues. Once everything checks out via DMARC reports, switch to -all (hard fail) to block unauthorized emails entirely. Testing your SPF record with an SPF checker before deployment is crucial. Remember, SPF only validates the envelope sender (MAIL FROM), not the visible "From" address. A properly configured SPF record not only secures email delivery but also provides valuable data for ongoing monitoring and deliverability optimization.
Implementing DKIM Correctly
After setting up SPF, move on to DKIM, which ensures message integrity through digital signatures. DKIM works by using a public/private key pair: the private key stays on your mail server to sign outgoing emails, while the public key is published in DNS under [selector]._domainkey.[domain]. For stronger security, use 2048-bit RSA keys, provided your DNS supports it. To simplify monitoring and isolate potential issues, use different selectors for different email streams - for instance, txn for transactional emails and news for newsletters. Rotate your DKIM keys every 4 to 18 months, ensuring the new public key is live in DNS before updating the private key on your server to avoid disruptions.
Review DMARC reports to spot unsigned or misaligned email traffic. If legitimate emails are missing DKIM signatures or failing alignment (where the d= domain doesn’t match the "From" address), address those issues promptly. You can also manually check email headers for a dkim=pass result to confirm that your DKIM setup is working as intended. This step not only secures your email but also ensures smooth monitoring.
Rolling Out DMARC Policies
DMARC ties everything together by verifying that the visible "From" address aligns with the domains validated by SPF and DKIM. Interestingly, around 75% to 80% of domains with DMARC records stay in monitoring mode because they discover legitimate sources failing authentication. Start with a p=none policy to monitor email traffic without blocking anything. Configure reporting URIs: use rua for aggregate reports that show overall traffic patterns and ruf for forensic reports with detailed diagnostics. Monitor these reports for at least 30 days to identify and fix issues before moving to stricter policies like p=quarantine or p=reject.
Add the fo=1 tag to your DMARC record to receive reports whenever SPF or DKIM fails, instead of waiting for both to fail. Use the insights from these reports to update SPF records, add missing DKIM signatures, or tweak aspf/adkim settings. Relaxed settings allow subdomain usage, while strict settings require exact matches.
To gradually enforce stronger policies, use the pct tag. For example, start by applying p=quarantine to 20% of your email traffic. As your configuration proves reliable, increase this percentage until you’re ready to implement p=reject to block unauthorized emails entirely. This phased approach ensures a smooth transition and sets the stage for consistent, ongoing monitoring of your email authentication setup.
Daily Compliance Monitoring Workflows
What to Monitor and Where to Find Data
Keep a close eye on your DMARC pass rate, as well as SPF and DKIM alignment rates and any unauthenticated traffic, on a daily basis. The main sources for this data are DMARC aggregate reports (RUA), which are XML files sent every 24 hours that summarize authentication traffic, and forensic reports (RUF), which provide detailed diagnostics, including subject lines and full headers for specific failures. Additionally, examine SMTP logs and email headers - specifically the Authentication-Results field - to gain real-time insights into SPF, DKIM, and DMARC outcomes. For Microsoft 365 users, it’s also important to monitor the proprietary compauth (composite authentication) result, which evaluates multiple authentication signals alongside internal trust indicators.
"DMARC only protects you if it's actively monitored and enforced. Leaving it at p=none indefinitely offers no protection against spoofing."
- Jack Zagorski, DMARCeye
Don’t forget to monitor subdomains. Each should have its own SPF record or be covered by a DMARC sp (subdomain policy) tag to prevent alignment issues. Many modern DMARC platforms can guide organizations to full enforcement (p=reject) in as little as 6 to 8 weeks by automating troubleshooting processes.
With monitoring in place, the next step is addressing common configuration mistakes that can impact these metrics.
Fixing Common Configuration Problems
One frequent issue is exceeding SPF's 10-lookup limit, which causes a permerror. To resolve this, flatten SPF records by replacing include: statements with direct IP addresses using macros or dynamic SPF tools. Another common mistake is having multiple SPF records - domains can only have one SPF TXT record. To fix this, merge all authorized IPs and mechanisms into a single entry.
DKIM alignment failures often occur when the signing domain (found in the d= tag) doesn’t match the domain in the "From" header. Check your DKIM configuration to ensure it uses the correct domain. If subdomains are involved, decide whether relaxed or strict alignment works best for your needs. Additionally, intermediaries like mailing lists or security appliances can break DKIM signatures by altering headers or message content. Implement ARC (Authenticated Received Chain) to preserve authentication results even when messages are modified during forwarding.
On the security front, upgrade any DKIM keys that are less than 2,048 bits, as weaker keys are vulnerable to attacks. Rotate these keys every 12 to 18 months to maintain strong security. Lastly, clean up your SPF record by removing outdated IP addresses or unused include: mechanisms to avoid IP recycling exploits, where attackers might misuse abandoned addresses.
| Issue | Symptom | Effective Resolution |
|---|---|---|
| SPF Lookup Limit | spf=permerror |
Flatten SPF records using macros or dynamic SPF tools |
| Multiple SPF Records | SPF Fail / Neutral | Combine all entries into a single TXT record |
| DKIM Alignment | DMARC Fail (DKIM Pass) | Ensure the d= tag matches the "From" domain |
| Body Hash Failure | dkim=fail |
Use ARC to handle intermediaries modifying content |
| Missing RUA Tag | No DMARC reports | Add rua=mailto:address@domain.com to the DMARC record |
| Weak DKIM Key | Security vulnerability | Upgrade to 2,048-bit RSA keys and rotate every 12–18 months |
Automated tools can simplify these fixes and help maintain compliance over time.
Using Tools to Automate Monitoring
Manually monitoring multiple domains or handling high email volumes can quickly become overwhelming. Automation tools like DMARCeye can make this process manageable by using AI to analyze daily aggregate reports. These tools transform complex XML data into user-friendly visualizations that clearly differentiate between authorized and unauthorized sending sources. For large-scale operations, they can even update authentication records across hundreds or thousands of domains simultaneously, saving significant time and effort.
Infraforge takes automation a step further by streamlining DNS setup for SPF, DKIM, and DMARC during domain provisioning. It offers pre-warmed domains, dedicated IPs, and real-time monitoring to identify potential deliverability issues before they escalate. By integrating with the Forge Stack, Infraforge provides automatic updates to authentication records and delivers actionable compliance insights. This is especially useful given that over 20% of marketing emails fail to reach inboxes, while proper authentication and email warm-up can improve deliverability by around 10% and boost open rates by up to 20%.
When choosing tools, prioritize those that support DKIM key rotation every 12 to 18 months and include real-time performance tracking, such as "heat scores" for inbox placement across major providers. For example, Warmforge - which also integrates with Forge Stack - offers email warm-up and deliverability monitoring for $10 per month (billed quarterly). It boasts high ratings, with 4.9/5 on G2 and 4.8/5 on Product Hunt. Start with a p=none DMARC policy when implementing automated monitoring to gather data without disrupting email delivery.
"Engagement is your lifeline to reputation as a sender. It is extremely important."
- Nick Schafer, Sr. Manager of Deliverability & Compliance, Sinch
Long-Term Compliance Management
Getting the initial setup right is just the beginning - staying compliant over time requires consistent attention and proactive management.
Managing Policies and Configurations
Email authentication isn’t a “set it and forget it” task. It demands ongoing care. Start by keeping an up-to-date sender inventory. This list should include every platform authorized to send emails on your behalf, such as CRMs, marketing tools, ticketing systems, and HR platforms. A current inventory not only simplifies troubleshooting but also helps you catch unauthorized email activity. Make sure to update this list whenever changes occur and assign responsibility for maintaining it to your marketing or IT operations team.
To avoid misconfigurations, use DNS templates for consistent authentication across domains and enforce strict change control processes. For subdomains that don’t send emails, publish a "deny all" SPF record (v=spf1 -all) and set your DMARC policy to p=reject to block spoofing attempts.
"DMARC isn't a 'set it and forget it' system. It's an evolving part of your domain's security posture."
- Jack Zagorski, DMARCeye
Think of DMARC as a long-term framework rather than a one-time setup. If you’re managing multiple domains, use the pct tag (e.g., pct=50) to enforce DMARC policies gradually, starting with a portion of your email traffic while monitoring results. Transitioning from p=none to p=quarantine and eventually to p=reject minimizes the risk of accidentally blocking legitimate emails.
Regular audits are key to ensuring your configurations remain effective and up to date.
Running Regular Compliance Audits
Quarterly audits are essential to ensure your authentication records are accurate and functioning properly. During these reviews, check that SPF records stay within the 10-lookup limit, confirm that DKIM keys are at least 2,048 bits, and analyze DMARC aggregate reports for unauthorized IP addresses or alignment issues. Test your email authentication setup with major providers like Gmail, Outlook, and Yahoo to ensure consistent results.
| Audit Activity | Frequency | Tools | Responsible Role |
|---|---|---|---|
| Review SPF Lookup Count | Quarterly | MxToolbox, Google Admin Toolbox | DNS Administrator |
| DKIM Key Rotation | 12–18 Months | OpenSSL, Provider Dashboard | Security Analyst |
| DMARC Report Analysis | Daily/Weekly | DMARCeye, DMARCian, Postmark | IT/Security Admin |
| Sender Inventory Update | Per Change | Internal Documentation/Spreadsheet | Marketing/IT Ops |
| Subdomain Policy Check | Bi-Annually | nslookup, DIG | DNS Administrator |
Rotate DKIM keys every 12 to 18 months to maintain strong cryptographic protection. Remove any outdated third-party services from your SPF records to reduce vulnerabilities. Regularly review DMARC pass rates and alignment trends to spot configuration drift or newly unauthorized senders.
Responding to Compliance Violations
If DMARC reports flag unauthorized email sources or spoofing attempts, act quickly. First, figure out whether the issue is caused by a misconfigured legitimate sender or a real security threat. For legitimate sources, update your SPF records or adjust DKIM alignment as needed. If it’s a confirmed spoofing attempt, alert your security team and tighten your DMARC policy immediately.
For cases where intermediaries like mailing lists or forwarding services disrupt DKIM signatures, implement Authenticated Received Chain (ARC) to preserve authentication results. After resolving each incident, conduct a root cause analysis to identify any gaps in your sender inventory or configuration processes.
Tools like Infraforge can help reduce the impact of compliance issues. By providing dedicated IPs and domain pools for email campaigns, Infraforge ensures that a problem with one domain doesn’t disrupt others. Its automated DNS setup and real-time monitoring catch misconfigurations early, and its integration with Warmforge helps track deliverability, ensuring your compliance efforts align with optimal inbox placement.
Conclusion
Today, SPF, DKIM, and DMARC aren't just recommendations - they're absolute necessities. Gmail and Yahoo now require these protocols for senders exceeding 5,000 emails daily. With Business Email Compromise scams racking up over $55 billion in global losses and nearly half of email senders struggling to avoid spam folders, proper email authentication has become the frontline defense against both security threats and delivery issues.
Staying compliant means constant vigilance. This includes tracking authentication pass rates, reviewing DMARC reports, keeping an updated sender inventory, and quickly addressing any violations. Add to that the complexity of managing DNS records and configuring policies, and the challenge only grows - especially for businesses operating at scale. Simplifying this process is no longer a luxury; it's a necessity.
That’s where Infraforge steps in. By automating tricky technical tasks like DNS setup, offering dedicated IPs, and providing real-time monitoring, Infraforge helps catch misconfigurations before they snowball into deliverability issues. For about $651 per month for 200 mailboxes, it offers a cold outreach infrastructure designed to streamline compliance, cutting setup time down to just five minutes.
Pair it with Warmforge, and you’ve got a powerful combination that not only ensures authentication compliance but also builds sender reputation. With DMARC adoption increasing among Global 2000 companies, it’s clear that staying ahead in email security is now a business-critical priority.
Start with a p=none policy for 30 days to monitor and gather data, then gradually tighten your settings as stability is confirmed. This step-by-step strategy ensures you remain secure and efficient as you scale your outreach efforts. With the right tools and infrastructure, you can achieve both reliable email delivery and growth in your campaigns.
FAQs
How do SPF, DKIM, and DMARC work together to protect your email from spoofing and phishing?
SPF works by checking the sender's IP address to confirm that only approved servers can send emails on behalf of your domain. DKIM takes it a step further by attaching a cryptographic signature to your emails, ensuring the message remains unchanged during its journey. DMARC brings these two protocols together, aligning the results of SPF and DKIM while giving email receivers clear instructions on how to handle messages that fail authentication.
Together, these protocols form a strong shield against email spoofing and phishing, safeguarding your brand’s reputation and helping your messages land in the right inboxes.
What mistakes should I avoid when setting up SPF, DKIM, and DMARC?
When setting up SPF, DKIM, and DMARC, it’s easy to make a few missteps that can lead to headaches down the line. Here are some common issues to watch out for:
- SPF alignment problems: If your SPF record doesn’t match the visible From domain, authentication might fail. Also, exceeding SPF’s 10-lookup limit or forgetting to include all legitimate email sources can cause delivery problems.
- DKIM vulnerabilities: Using outdated or weak DKIM keys, or neglecting to rotate them periodically, can leave your setup exposed to security risks.
- DMARC missteps: Jumping straight to a strict DMARC policy without first monitoring alignment and reviewing reports can result in legitimate emails being flagged as spam or outright rejected.
To steer clear of these issues, take the time to double-check your DNS records, regularly monitor email authentication reports, and thoroughly test your configuration before enforcing strict policies. A well-implemented setup not only improves email deliverability but also safeguards your domain against spoofing and phishing attempts.
How does Infraforge simplify email authentication and improve monitoring?
Infraforge takes the hassle out of email authentication by automating the setup of critical components like SPF, DKIM, and DMARC records. When you add a domain, it automatically creates a secure DKIM key, configures SPF records with dedicated IPs, and applies a DMARC policy in monitoring mode. This hands-free approach helps avoid manual errors and ensures your email setup meets compliance standards right from the start.
But it doesn’t stop at setup. Infraforge keeps an eye on DMARC reports, highlights authentication issues with easy-to-read visualizations, and sends alerts so you can address problems quickly. Its private email infrastructure also pre-warms domains and mailboxes, boosting sender reputation before your campaigns even begin. With dedicated IPs and API-driven workflows, Infraforge delivers consistent email performance and offers a scalable solution for large-scale outreach - all while minimizing the chances of configuration mistakes.