OAuth vs API Keys: Secure Email Integration
When it comes to securing your email campaigns, the choice between API keys and OAuth matters. API keys are simple and quick to set up, often ideal for smaller teams or basic integrations. However, they come with risks like full-access exposure if compromised. OAuth, on the other hand, provides a more secure, token-based approach with temporary permissions and user-level tracking, making it better suited for larger operations or high-risk environments.
Key Points:
- API Keys: Static credentials, easy to implement, but risky if leaked. Best for small teams or straightforward use cases.
- OAuth: Dynamic tokens with scoped permissions, more secure but complex to implement. Ideal for multi-user setups or enterprise needs.
- Security Practices: Use HTTPS, rotate credentials, monitor activity, and store keys securely to protect your email system.
- Compliance: Adhere to laws like CAN-SPAM and GDPR by managing access and maintaining detailed logs.
Quick Comparison:
| Factor | API Keys | OAuth |
|---|---|---|
| Setup Complexity | Simple | More complex |
| Security Model | Static credentials | Dynamic tokens with expiry |
| User Management | Shared access | Individual permissions and tracking |
| Scalability | Challenging at scale | Scales well with automated processes |
| Revocation Speed | Manual | Centralized and immediate |
For smaller setups, API keys may suffice. But if your email operations involve multiple users, sensitive data, or compliance requirements, OAuth offers stronger protections and control.
API Keys: Simple Authentication for Email Systems
API keys act as static digital credentials, providing a straightforward way to authenticate access to your email infrastructure. Essentially, they work like a handshake: your application includes the API key - a random alphanumeric string - in the header of every request. The email service then verifies the key and processes your request if it matches an active account.
How API Keys Work
API keys operate as static credentials. Once generated, they remain unchanged unless you manually rotate or revoke them. When you sign up for an email service, the provider issues a key linked to your account. This key grants access to your email service for your entire application, regardless of which team member performs an action. Your cold email platform uses this key to connect with services like SendGrid, Mailgun, or Amazon SES.
Most email providers require the API key to be included in the request header in a specific format. For instance, many services expect an "Authorization" header with a value like Bearer [your-api-key]. Others might use a custom header such as X-API-Key: [your-api-key]. While the exact implementation can vary, the underlying principle is consistent across platforms.
This simplicity is both the strength and the potential weakness of API keys.
API Keys: Pros and Cons
| Advantages | Limitations |
|---|---|
| Easy to implement – Quick setup with minimal configuration | High risk if exposed – A leaked key gives full access to your account |
| Widely supported – Almost all email APIs accept API keys | All-or-nothing access – Lacks granular permissions to limit functionality |
| Low development effort – Simple integration without complex workflows | No user-level tracking – Can't identify individual users' actions |
| Key rotation challenges – Changing keys can disrupt multiple services |
The simplicity of API keys makes them ideal for small teams or quick integrations. For instance, you can get a cold email system running within minutes of receiving your API key. This ease of use is why many developers choose API keys as the starting point for email automation systems.
However, as your operations grow, the security limitations of API keys become more apparent. A compromised key can provide attackers with unrestricted access, allowing them to send emails, access contact lists, or even change account settings. Unlike OAuth tokens, API keys don’t offer scoped permissions that restrict access to specific functions. They also represent the entire application, making it impossible to track which team member performed a specific action or enforce user-level access controls.
API Key Security Best Practices
To mitigate the vulnerabilities of API keys, follow these security best practices:
- Use HTTPS: Always transmit API keys over HTTPS to prevent interception during transit. This helps protect against network-level attacks.
- Avoid hardcoding keys: Never embed API keys directly into your application code or commit them to version control systems like GitHub. Instead, store them as environment variables or use secret management services to reduce the risk of accidental exposure.
- Enable IP allowlisting: If supported by your email provider, restrict API key usage to specific IP addresses. This adds an extra layer of security, even if the key is compromised.
- Rotate keys regularly: Change your API keys every 90 days or sooner if you suspect any issues. Schedule rotations during low-traffic periods to minimize disruptions, and test the process in a staging environment before applying it to production.
- Monitor usage: Use your email provider’s dashboard or logging tools to track API key activity. Set up alerts for unusual patterns, such as requests from unexpected IP addresses or sudden spikes in usage.
- Store keys securely: Use encrypted storage solutions instead of plain text files or unsecured databases. Consider tools like AWS Secrets Manager, Azure Key Vault, or HashiCorp Vault. These services often include features like automatic rotation and detailed access logs for added security.
OAuth: Advanced Security for Email APIs
OAuth provides a dynamic and secure way to authenticate email APIs, using temporary tokens instead of static credentials. This system is built on the concept of delegated authorization, allowing users to grant your application specific permissions to access their email services - without ever sharing their login credentials. It's become a go-to choice for modern API security, especially in enterprise settings where different team members often need tailored access levels to email systems.
How OAuth Works for Email APIs
OAuth operates through a multi-step process that generates short-lived access tokens rather than permanent credentials. For example, when your cold email application connects to an email service like the Gmail API or Microsoft Graph, it redirects users to the email provider’s secure authorization page. Users log in there, and once authenticated, the provider sends back an authorization code. Your application then exchanges this code for an access token with limited permissions, and often a refresh token as well.
These access tokens come with scoped permissions, which define exactly what your application can and cannot do. For instance, Gmail’s API offers a variety of permission scopes, giving you fine-grained control over the data and functions your app can access.
If a token is intercepted, its short lifespan minimizes potential damage. Additionally, user credentials stay securely with the email provider, offering a level of protection far beyond what API keys can provide. This layered approach to security makes OAuth a standout choice for safeguarding email APIs.
OAuth: Benefits and Drawbacks
| Advantages | Limitations |
|---|---|
| Short-lived tokens – Automatically expire to reduce security risks | Complex implementation – Requires time and technical expertise |
| Granular permissions – Allows precise control over access | Token management overhead – Refresh cycles and expiration add complexity |
| User-specific tracking – Enables detailed action logs and user-level controls | Dependency on third parties – Relies on external authorization servers |
| No credential sharing – Users never need to share passwords | Potential disruptions – Token refresh failures can interrupt operations |
| Centralized revocation – Users can revoke access instantly via account settings | Higher infrastructure costs – Secure token storage and management are required |
OAuth’s granular permissions and centralized revocation are particularly useful in team environments. For instance, if a team member leaves the organization, they can revoke your app’s access to their email account through their Google or Microsoft account settings. This flexibility is a major advantage over API keys, which lack such individual control.
Additionally, OAuth’s scoped permissions let you request only the access your app genuinely needs, adhering to the principle of least privilege. This minimizes risk while maintaining functionality.
However, implementing OAuth isn’t without its challenges. It demands secure token storage, automatic refresh mechanisms, and robust error handling for scenarios like expired tokens, unavailable authorization servers, or revoked permissions. Your application must be equipped to handle these situations gracefully to ensure a seamless user experience.
When to Choose OAuth for Email Infrastructure
So, when does it make sense to use OAuth? It’s an excellent choice when your email operations involve multiple team members with varying access needs. If your cold email platform serves diverse clients who need to connect their own email accounts, OAuth provides a secure and user-friendly authentication model that API keys struggle to match.
Enterprise environments are particularly well-suited for OAuth. Large organizations often require detailed logs to track who performed specific actions, and OAuth’s ability to tie tokens to individual users makes this straightforward. This feature is especially valuable in industries with strict compliance requirements, such as healthcare, finance, or law.
OAuth is also ideal for multi-tenant applications where each client connects their own email systems. Instead of juggling numerous API keys across different providers, OAuth offers a standardized process that works across major platforms like Gmail, Outlook, and Yahoo.
For high-volume email senders, OAuth’s automatic token refresh capabilities can reduce the hassle of manual API key rotations, saving time and effort as your operations grow. While the initial setup may require more resources, the long-term benefits of improved security and reduced maintenance are hard to ignore.
That said, OAuth isn’t always the best fit. For smaller teams with straightforward email needs, the complexity of implementing OAuth might outweigh its benefits. In such cases, API keys can still provide adequate security with significantly less effort.
API Keys vs OAuth: Direct Comparison
Choosing between API keys and OAuth comes down to weighing simplicity against more advanced functionality. Each method caters to specific needs in email integration, and understanding their differences can help improve operations and enhance security.
Feature Comparison: API Keys vs OAuth
The differences between API keys and OAuth become clear when you break them down by key factors:
| Factor | API Keys | OAuth |
|---|---|---|
| Setup Complexity | Simple – generate and store a single key | More complex – involves authorization flows and token management |
| Implementation Time | Quick to implement | Takes longer due to additional configuration and error handling |
| Security Model | Relies on static credentials that require manual rotation | Uses dynamic tokens that automatically expire |
| User Management | Shared access point | Supports individual user permissions and tracking |
| Scalability | Challenging as manual key management grows | Scales smoothly with automated token refresh processes |
| Compliance Tracking | Basic logging capabilities | Detailed audit trails with user-specific attribution |
| Cost of Maintenance | Lower, with minimal ongoing management | Higher, due to token storage and refresh infrastructure |
| Revocation Speed | Manual and potentially slower | Faster, with centralized controls for immediate revocation |
This breakdown helps clarify which option might be better suited for your needs.
How to Choose the Right Authentication Method
When deciding between API keys and OAuth, consider your operational scale, security needs, and team expertise. For smaller setups with fewer users, API keys are a straightforward and quick solution. However, as operations expand, managing API keys manually can become cumbersome. Larger organizations often prefer OAuth for its fine-grained access controls, automated token processes, and detailed audit trails, which are essential for maintaining security and compliance.
Additionally, think about your team's technical skills. API keys are easier to implement and require only basic programming knowledge. On the other hand, OAuth demands a deeper understanding of secure integration practices and token management. Ultimately, the right choice depends on your security priorities, the size of your operation, and your team's technical capabilities.
Infraforge and Secure Email Infrastructure Solutions
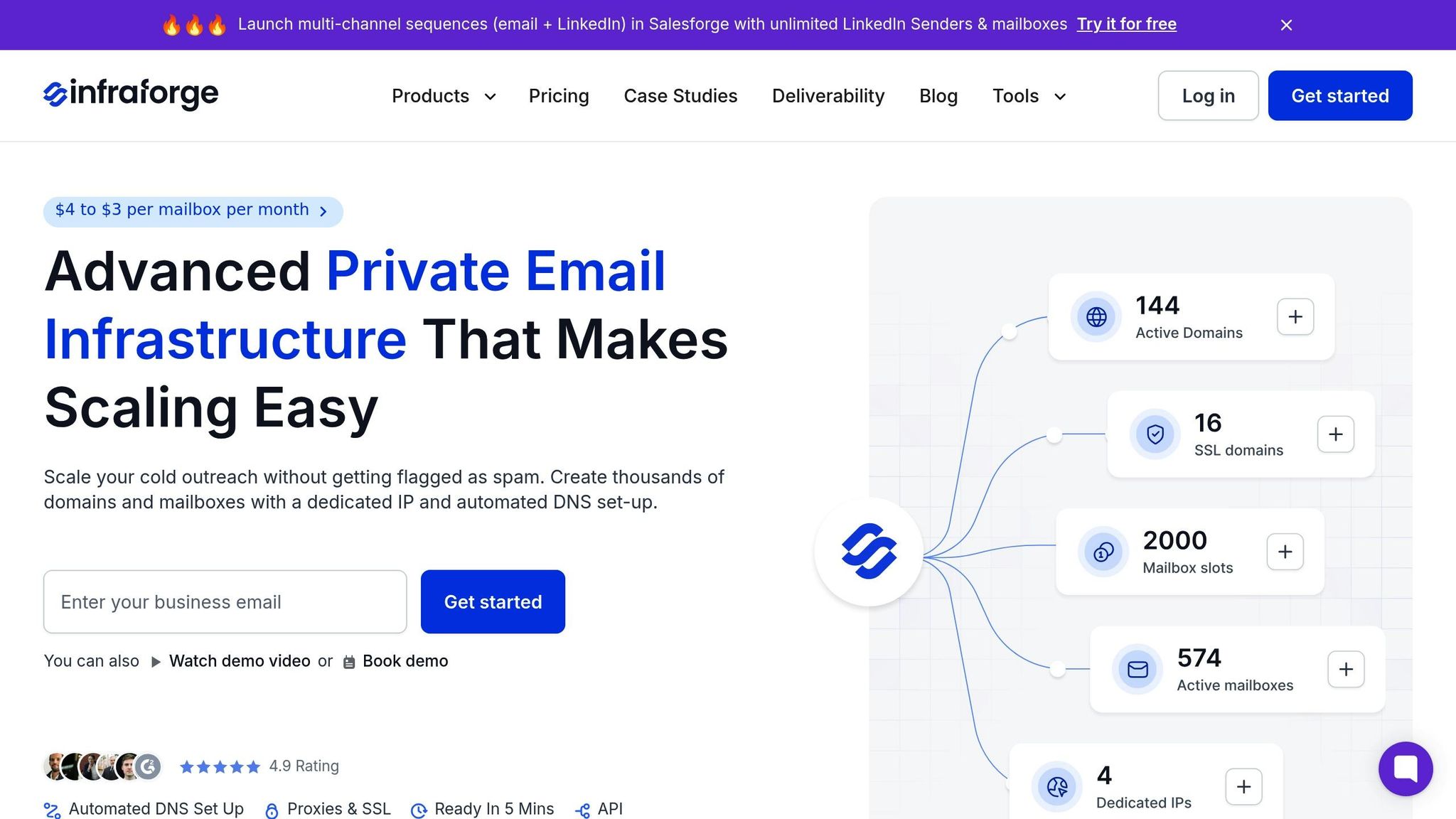
For cold outreach, having a secure and reliable email infrastructure is non-negotiable. Infraforge provides a private email system designed for strong security and centralized control. This setup gives businesses the ability to oversee email deliverability while maintaining compliance. By utilizing both API key and OAuth methods, Infraforge ensures a secure and scalable email infrastructure tailored to meet modern demands.
The platform also tackles the challenge of maintaining high performance as outreach efforts grow. This is bolstered by Infraforge's advanced API security features, which enhance the platform's reliability.
Infraforge's API Security Features
Infraforge’s API security framework is built on a dedicated infrastructure that supports both OAuth and API key authentication. It automates the configuration of essential email authentication protocols - such as DMARC, SPF, DKIM, and custom domain tracking - ensuring that domains follow industry standards to prevent spoofing and authentication errors.
To further secure communications, SSL and domain masking encrypt data in transit while enabling the use of branded domains without exposing core ones. This also strengthens OAuth-based security. Additionally, multi-IP provisioning spreads email sending across multiple IP addresses, reducing the likelihood of blacklisting and improving overall deliverability.
Infraforge vs. Other Email Infrastructure Providers
Unlike providers that depend on shared infrastructure, Infraforge operates on a private system, offering enhanced security and control. For instance, competitors like Maildoso rely on shared systems with dynamic IP rotation, which can compromise security and deliverability. Infraforge’s private infrastructure avoids these pitfalls, making it a better choice when secure authentication and stable deliverability are priorities.
Scaling Cold Email with Infraforge's API
Infraforge’s API supports both API key and OAuth authentication, simplifying integration with tools like Salesforge. The platform facilitates seamless connections with automation and email-sending software, allowing users to track their Mailbox Reputation Score in real time.
At a cost of about $2.50 per mailbox per month with a private IP, Infraforge delivers a competitively priced solution for secure email infrastructure. Its API automates key tasks like mailbox provisioning, domain setup, and DNS configuration, ensuring that security measures remain intact even as outreach scales. This makes it an ideal choice for businesses aiming to run secure and scalable email campaigns.
Email API Security Best Practices
Securing email APIs goes beyond simply picking a method like API keys or OAuth. The real work lies in setting up and managing these systems to safeguard your cold email operations against breaches and compliance risks.
Secure Setup for API Keys and OAuth
When using API keys or OAuth tokens, follow these steps to keep your system secure:
- Always use HTTPS/TLS to encrypt credentials during transmission. This prevents man-in-the-middle attacks and ensures secure communication.
- Rotate credentials regularly to reduce the risk of exposure if they’re ever compromised.
- Apply the principle of least privilege. Only grant the API permissions that are absolutely necessary. For example, an email automation tool might only need access to send emails, not your entire account.
- Monitor API activity to catch unusual behavior. Set alerts for spikes in requests, repeated login failures, or access attempts from unexpected locations.
- Store credentials securely using environment variables or secret management tools, keeping sensitive information out of your codebase.
- Handle errors carefully. Avoid exposing sensitive details in error messages or logs. Instead, log security events internally for analysis while showing generic error messages to users.
These practices not only enhance security but also align with key US compliance requirements.
US Compliance Requirements for Email APIs
If you're running cold email campaigns in the US, meeting compliance standards is non-negotiable. Here’s what you need to keep in mind:
- CAN-SPAM Act compliance: Your API must support features like accurate sender identification, a valid physical address, and an easy way for recipients to unsubscribe.
- GDPR considerations: If you handle data from EU residents, your system should allow data portability, deletion, and maintain audit logs for API interactions involving personal data.
- Industry-specific regulations: Sectors like healthcare or finance may have additional requirements, such as stricter authentication protocols or detailed audit trails.
- Data residency rules: With evolving state privacy laws, you’ll need to track where data is processed and maintain records to support compliance and data access requests.
- Incident reporting: Be ready to respond quickly to breaches. Comprehensive logging can help trace access events and support an effective response.
- Regular compliance audits: Periodically review your API security setup, including authentication methods, credential management, and access controls, to demonstrate your commitment to secure email practices.
Conclusion: Choosing Your Email Authentication Method
Selecting the right email authentication method boils down to balancing your security needs with the complexity of implementation. API keys are great for quick setups and straightforward authentication, making them a go-to for testing environments, internal tools, or cases where you're handling non-sensitive data. However, their simplicity can turn into a vulnerability when dealing with user-facing applications or sensitive email operations. On the other hand, OAuth provides a more secure, token-based approach, especially suited for high-risk scenarios.
OAuth stands out when you need strong security and precise access control. Its token-based system allows temporary, user-approved access, which significantly cuts down on security risks. Research shows that while 70% of developers lean toward API keys for their ease of use, over 80% of data breaches stem from poor access controls. Interestingly, organizations using OAuth report a 30% drop in security incidents and a 30% boost in user engagement.
For cold email campaigns, especially those involving large-scale operations or diverse teams, strong access controls are a must. If your campaigns involve multiple team members accessing the system, OAuth's user-specific permissions and audit trails become indispensable. However, for simpler setups or internal automation, API keys can work just fine - as long as they're paired with solid security practices.
Given these considerations, many cold email operators turn to platforms that support both methods. Infraforge, for example, offers a flexible solution with API keys and OAuth, along with features like dedicated IPs, automated DNS setup, and pre-warmed domains. These tools ensure your email infrastructure remains compliant and your campaigns deliver effectively. Additionally, its API allows programmatic scaling while adhering to US compliance standards, including the CAN-SPAM Act.
Keep in mind, authentication needs can change over time. Many organizations start with API keys for their simplicity and later transition to OAuth as their security requirements grow. From day one, focus on proper credential management, regular key rotations, and thorough monitoring. Secure authentication not only protects your sender reputation but also plays a crucial role in the success of your email campaigns.
FAQs
When should you choose OAuth instead of API keys for email integration?
OAuth stands out as the smarter option when security and precise access control are top priorities. With OAuth, you can assign specific permissions to each token - like read-only or write access - helping to avoid the risks of overly broad access that often come with API keys. Plus, OAuth tokens usually come with a limited lifespan and can support multi-factor authentication, making them an excellent choice for tasks like user-facing email integrations or managing sensitive data.
Unlike API keys, which tend to offer unrestricted, all-or-nothing access, OAuth shines in scenarios requiring third-party integrations, social logins, or fine-tuned control over data and actions. This makes it a go-to solution for applications where security and compliance are non-negotiable, especially in email infrastructure.
What are the best practices for small teams to secure API keys?
Small teams looking to keep their API keys secure can take a few straightforward steps. First, limit access to these keys by using IP whitelisting and setting usage limits. It's also crucial to avoid embedding keys directly in client-side code, as this makes them vulnerable to theft. A better approach is to store them safely on the server and manage API requests through a backend or proxy.
Another important step is to rotate keys frequently. This reduces the damage if a key is ever exposed and ensures only the right users or systems have access. By adopting these practices, small teams can better protect their applications from unauthorized access and keep their integrations secure.
How does using OAuth for email APIs help meet compliance requirements in regulated industries?
Using OAuth with email APIs offers a secure, token-based access method that eliminates the need for sharing passwords - an essential feature for industries with strict regulatory requirements. This approach helps businesses adhere to standards like GDPR, HIPAA, and PCI DSS by ensuring sensitive data is accessed and transmitted with a high level of security.
Another key advantage of OAuth is the ability to maintain detailed audit trails, which is crucial for industries managing protected information. Features such as token expiration and fine-grained permission settings minimize risks, while advanced configurations can add extra layers of security for high-risk scenarios. By integrating OAuth, organizations can better meet regulatory obligations and safeguard sensitive communications.