Azure SMTP Server: Good or Bad for Cold Emails?
Azure SMTP looks appealing at first because it offers built-in SMTP support through Azure Communication Services for sending emails.
It provides a structured way to send emails, with security checks, sender authentication support, and centralized control.
If you already use Azure, this can feel like a familiar and reliable place to start.
But cold email is not the same as a regular application email.
Before sending anything, it’s important to understand how Azure SMTP actually works, what kind of setup it requires, and how much control and flexibility it gives you for outbound outreach.
In this guide, we’ll walk through Azure SMTP in simple terms, break down what’s involved, and help you decide whether it truly fits your cold email use case or if another approach makes more sense
Key Takeaways
- Azure SMTP is designed for application and system emails, not inbox-based cold outreach workflows.
- Email sending in Azure SMTP is tied to Microsoft Entra application identities, not individual mailboxes.
- Domains must be Azure-managed or manually verified custom domains before any sending can occur.
- SPF and DKIM are required for sending, but DNS setup for custom domains still involves manual steps.
- Built-in security, fraud detection, and hygiene checks are always enforced and cannot be tuned for cold email.
z - Azure SMTP provides delivery status, logs, and basic engagement data, but no warmup, sender rotation, or deliverability controls.
- Scaling cold email with Azure SMTP requires repeated manual setup of domains, identities, roles, and credentials.
- Infraforge bundles SMTP, domains, mailboxes, DNS automation, warmup, rotation, and deliverability monitoring into a single outbound-focused system.
- Teams running cold email at scale benefit from Infraforge’s automated setup and reduced operational overhead compared to Azure SMTP.
Get Infraforge to set up SMTP, domains, and mailboxes automatically and start sending your cold emails in minutes.
What “Good or Bad” Means for Cold Email
In cold email, “good” or “bad” is not subjective. It shows up in how easily you can send, scale, and stay deliverable over time.
A setup is considered “good” for cold email when:
- Sending reputation is isolated per domain and mailbox, limiting blast radius when issues occur
- Domains and inboxes can be created, replaced, or rotated without redoing the entire setup
- SPF, DKIM, and DMARC are applied consistently across all sending domains
- Warmup and sending limits are enforced automatically, not left to manual control
- Scaling from a few inboxes to dozens does not add operational complexity
- Failures (blocks, bounces, restrictions) are visible and actionable
A setup is considered “bad” for cold email when:
- Sending identity is centralized, causing one issue to affect all outgoing email
- Domains are difficult to verify, rotate, or replace once sending begins
- Authentication depends on manual DNS changes for each domain
- Warmup, domain and IP rotation, and sending behavior must be managed externally
- Scaling increases setup steps rather than repeating a proven process
- Blocks or restrictions happen without clear feedback or control
In practice, “good” cold email infrastructure reduces setup effort as volume increases.
“Bad” infrastructure makes scaling riskier and harder the more you send.
What Azure SMTP Server Is Built For
Azure SMTP is designed for sending emails from applications and internal systems, not inbox-based outreach.
It provides a centralized, authenticated SMTP service where email sending is controlled at the application level.
Emails are sent on behalf of Microsoft Entra applications, with permissions managed through roles and credentials rather than individual mailboxes.
This model suits transactional and system emails such as notifications, alerts, and account messages.
Azure SMTP assumes stable domains and predictable sending patterns.
It prioritizes security, identity control, and compliance over flexibility, rotation, or outreach-specific workflows.
As a result, Azure SMTP fits environments where email is a controlled system function rather than a scalable outbound channel.
How Email Sending Works in Azure SMTP
Here’s how email sending works in Azure SMTP, step by step:
An application connects to Azure SMTP
First, an application connects to Azure’s SMTP endpoint (smtp.azurecomm.net) using TLS.
The connection is authenticated with an SMTP username that maps to a Microsoft Entra application and a password that is the app’s client secret.
Emails are sent from a set domain
Emails are then sent using either an Azure-managed domain or a verified custom domain.
Azure enforces sender authentication and will not process messages from unverified domains.
The sender identity is verified
Before delivery, outgoing messages pass through Azure’s built-in security, hygiene, and abuse-detection checks.
Emails that violate these rules may be delayed, modified, or blocked.
Azure sends and tracks the email
Once everything is verified, Azure SMTP sends the email to the mail servers and records delivery status for tracking.
The application gives the email to Azure, Azure checks it, and the email is sent through Azure’s SMTP system.
Microsoft Azure SMTP Server Authentication and Access Configuration (Step-by-Step)
Before Azure SMTP can send emails, a few things need to be set up.
Here’s the full SMTP setup you need:
Step 1: Have Azure email services ready
Before anything else:
- Create an Azure account
- Setup Azure Communication Services resource

- Get Email Communication resource connected to it
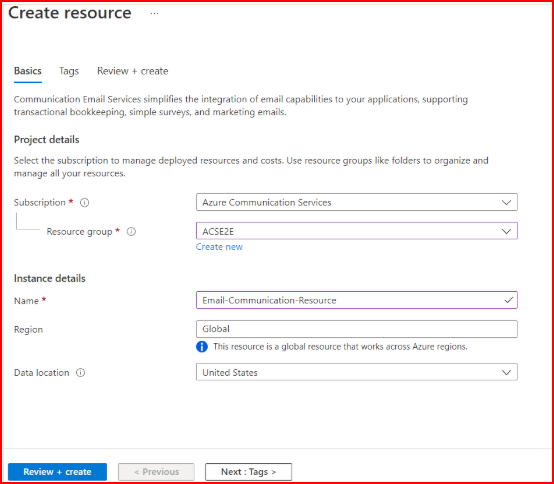
This is the base Azure uses for sending emails.
Step 2: Decide which domain will send emails
Azure needs to know which domain emails will come from.
You can use:
- An Azure-managed domain, or
- Your own custom domain
If you use your own domain:
- You must verify it before sending emails
Step 3: Create an app identity in Microsoft Entra
Azure does not allow random systems to send emails.
So you create an application in Microsoft Entra.
- This app acts like an ID
- It represents the system that will send emails
So, that approval is handled by Microsoft Entra.
Step 4: Give the app permission to send emails
You must:
- Go to the Azure Communication Services resource
- Assign the Communication and Email Service Owner role to the app
This step tells Azure the app is allowed to send emails.
Step 5: Create an SMTP username
Now Azure needs a login name for SMTP.
You:
- Create an SMTP username
- Link it to the Microsoft Entra app
This username is used to identify the sender during SMTP login.
Step 6: Create a secret to use as the password
SMTP also needs a password.
For Azure SMTP:
- The client secret of the Entra app is used as the password
This secret proves the app’s identity.
Step 7: Use these details in SMTP settings
Finally, add these details to the application SMTP settings:
- SMTP server: smtp.azurecomm.net
- Port: 587 or 25
- TLS: Enabled
- Username: SMTP username
- Password: Client secret
After this, Azure recognizes the app and allows it to send emails.
Might be helpful for you: Common SMTP Errors and Fixes
Outbound Security and Email Hygiene in Azure SMTP
Azure SMTP applies basic security and hygiene checks to outgoing emails as part of its normal sending process.
Built-in security checks
Azure SMTP applies mandatory security and hygiene controls to all outbound email.
These checks are built into the service and run automatically on every message.
Email hygiene and protection
Outgoing emails are scanned for malware, unsafe attachments, and suspicious content before delivery.
These protections are part of Azure’s standard email pipeline and cannot be disabled or customized.
Content and Link Inspection
Azure evaluates message content and embedded URLs to detect phishing, fraud, or policy violations.
Emails that trigger these checks may be blocked or filtered before reaching recipients.
Fraud and misuse control
Azure SMTP checks outgoing emails for signs of abuse or misuse.
It looks for unusual sending patterns or activity that may seem unsafe.
To do this, Azure uses built-in transport rules that run automatically. If an email triggers these rules, it may be blocked or restricted before it reaches the recipient.
Policy-driven controls
All outbound emails follow internal rules and policies set by Azure.
These rules control how emails are processed and delivered.
They are managed entirely by Azure and apply the same way to all senders, with no custom rules for individual teams or campaigns.
Limited sender control
Senders do not have control over these checks.
You cannot change how strict the rules are, skip certain checks, or override a decision made by the system.
Emails must meet Azure’s security and hygiene standards in order to be sent.
Top SMTP Security Practices for Cold Emailing
What Visibility Azure SMTP Provides After Sending
After emails are sent through Azure SMTP, Azure provides basic visibility into what happens next.
- Azure SMTP shows delivery status for emails sent from the application, with updates available in near real time. Each email is tracked using a message ID.
- Azure keeps request-level logs for sent emails. These logs include message IDs and recipient details and are mainly used for troubleshooting or auditing when something goes wrong.
- Azure provides an Insights dashboard that shows overall email activity. This helps teams understand sending volume and general outcomes, rather than individual campaign performance.
- Azure SMTP also supports basic engagement tracking, including bounces, blocks, opens, and clicks. This gives a general idea of how emails behave after sending.
Azure SMTP Limitations for Cold Email Use Cases
- Built mainly for application emails, not cold outreach
Azure SMTP is designed for system and B2C emails. Cold email workflows usually need more flexibility than an application-first setup. - Setup takes time before you can send anything
You need Azure Communication Services, an email resource, domains, Microsoft Entra apps, roles, SMTP usernames, and secrets. For cold email, this feels heavy before even starting. - Identity and access setup is technical
SMTP access depends on Microsoft Entra apps, roles, and client secrets. This is more complex than setups built only for cold outreach. - Security and hygiene rules are always on
Azure runs built-in security, fraud detection, and hygiene checks on every email. These rules cannot be adjusted for cold email experiments. - Domains must be verified and managed carefully
Emails can only be sent from Azure-managed or verified custom domains. Quick testing or frequent domain rotation is slower. - DNS setup is not fully hands-off
Azure supports SPF and DKIM, but custom domains still need proper setup during verification. This adds extra steps compared to tools that automate DNS by default.
- No built-in warmup or sender rotation
Azure SMTP does not include mailbox warmup, pre-warmed domains, or sender rotation for cold email use cases. - Scaling domains and mailboxes is manual
Creating and managing many domains or mailboxes requires repeated setup. Tools like Infraforge are built to handle this in bulk. - Limited clarity when emails are restricted
You can see delivery status and basic engagement, but Azure does not clearly explain why some emails are blocked by internal checks. - Monitoring is system-focused, not outreach-focused
Logs and analytics help with diagnostics, but they are not designed to manage or improve cold email campaigns.
Best Outbound-focused alternative to Azure SMTP: Infraforge
Infraforge is a cold email infrastructure that includes SMTP sending and is built specifically for outreach.
It gives you SMTP, domains, mailboxes, DNS setup, warmup, and deliverability tools.
Infraforge lets you set up domains and mailboxes quickly, without going through long technical steps.
DNS records like SPF, DKIM, DMARC, and tracking are handled automatically when you add a domain.
It also supports pre-warmed domains and mailboxes, which helps teams start sending sooner.
On top of that, Infraforge is designed to handle sender rotation, smart sending limits, and ongoing deliverability monitoring.
Another important part is flexibility.
Infraforge works with any sending software that supports SMTP, so you’re not locked into a single tool or workflow.
You can plug it into your existing setup and focus on outreach.
Conclusion
When you look at Azure SMTP, it is mainly focused on sending emails from applications.
It helps teams send emails in a secure and controlled way, with authentication, domain checks, and built-in security handled inside Azure.
This works well if sending emails from apps or B2C systems is the main goal.
But when a cold email is involved, you require more than just sending.
You also need to manage domains, mailboxes, warmup, rotation, and ongoing deliverability, and Azure SMTP keeps its scope limited to the sending layer.
Infraforge gives SMTP sending, including domain and mailbox setup, automated DNS, warmup, sender rotation, and deliverability monitoring.
This keeps infrastructure and deliverability connected instead of being handled as separate pieces.
Get started with Infraforge and set up your domains, mailboxes, SMTP, and deliverability in one place